









 |
|
| Example - Rationale |
|
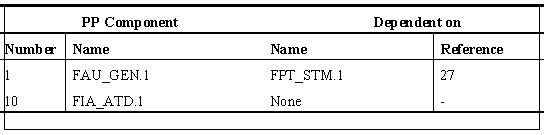
| Sample Dependency |
|
 |
 |
 |
 |
 |
 |
|
| Approach taken |
||||||
| ¨ | Assign each
Security Functional |
|||||
| Requirement a
reference number |
||||||
| ¨ | Draw up a table
covering all functional |
|||||
| components, e.g. |
||||||
 |
|
| 600.436 High- |
|
| Assurance
Systems |
|
| Fall
01/Protection Profiles |
| 10 |